By TDWAS
If you are looking at the booming cybersecurity market and thinking, “I missed the boat because I can’t write code,” you are looking at the wrong part of the boat.
While the media focuses on hackers in hoodies, the industry is quietly desperate for professionals who can manage strategy, policy, and risk. This is the domain of GRC (Governance, Risk, and Compliance).
If you come from a background in finance, law, healthcare, administration, or project management, you are not starting from scratch. You are starting with the exact skillset GRC managers need.
What is GRC in Cybersecurity?
Definition: GRC stands for Governance, Risk, and Compliance. It is the strategy ensuring an organization follows its own rules (Governance), protects against threats (Risk), and adheres to laws and regulations (Compliance). Unlike technical cybersecurity roles that focus on configuring firewalls, GRC focuses on policy, audits, and business logic.
Phase 1: The Mindset Shift (Transferable Skills)
Before you learn a single technical concept, you need to understand what you are already bringing to the table. In GRC, “soft skills” are actually “hard requirements.”
- Project Management: Essential for managing security audits and compliance timelines.
- Finance/Banking Experience: This experience translates directly to an understanding of regulatory pressures (e.g., SOX, PCI-DSS).
- Healthcare Experience: Provides a deep understanding of data privacy laws like HIPAA/PHIPA.
- Customer Success: Vital for communicating difficult risk scenarios to non-technical stakeholders.
Action Item: Rewrite your resume to highlight these transferable skills. You are not a “newbie”; you are an experienced professional pivoting domains.
Phase 2: What You Actually Need to Learn (And What to Ignore)
The biggest mistake career switchers make is trying to learn everything. You do not need to know how to penetration test a server to work in GRC.
The “Must-Haves” for GRC
- The Vocabulary: Master the CIA Triad (Confidentiality, Integrity, Availability). This is the foundation of all security decisions.
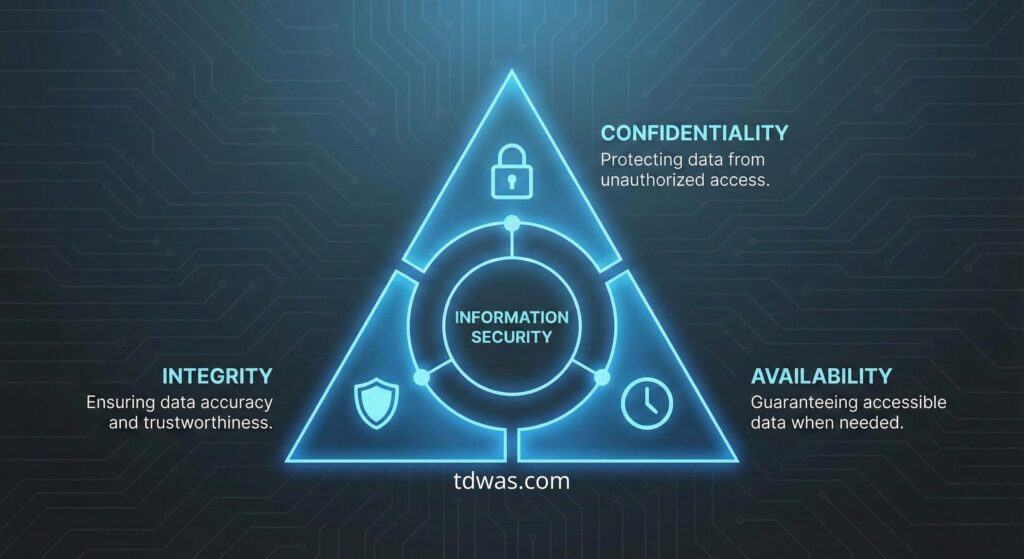
- The Frameworks: You don’t need to memorize them, but you must understand their purpose:
- NIST & ISO 27001: The global gold standards for security management.
- GDPR / CCPA: The laws governing data privacy and user rights.
- PCI-DSS: The strict rules for handling credit card data.
- Risk Management: Learn how to create and maintain a Risk Register, and how to calculate Inherent vs. Residual risk.
The “Distractions” (What You Can Skip)
- Python/Bash Scripting: Nice to have, but not required for entry-level GRC Analyst roles.
- Deep Networking (OSI Layers 1-3): You need high-level conceptual knowledge, not engineering-level configuration skills.
- Ethical Hacking Tools: You do not need to learn Metasploit, Burp Suite, or Kali Linux.
Phase 3: The GRC Certification Strategy (2025-2026)
Certifications are expensive. Don’t waste money on the wrong ones.
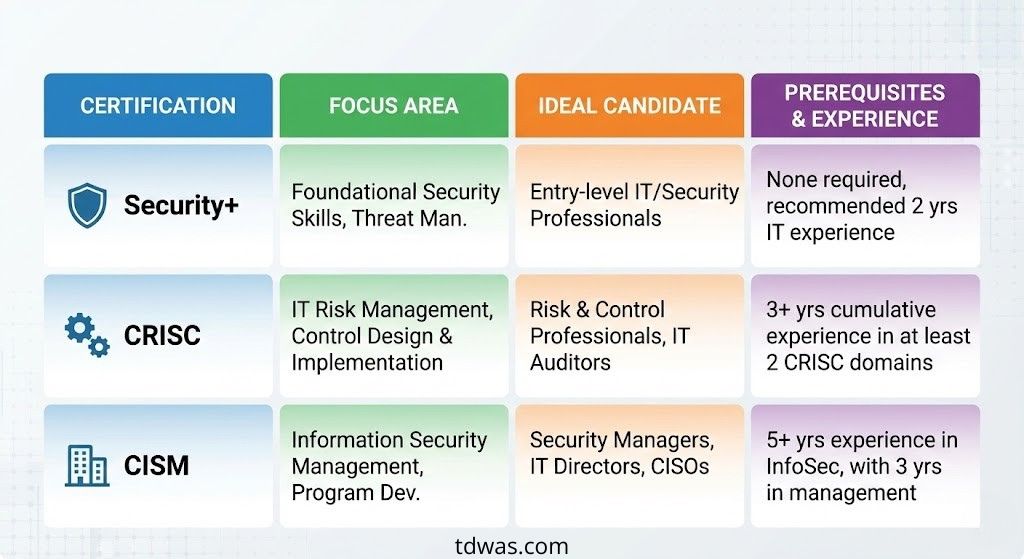
1. The Entry-Level Standard
- CompTIA Security+: This is the non-negotiable entry ticket. It proves you speak the language of security without requiring you to be an engineer.
2. The Mid-Career Goals (2-3 Years Experience)
- CRISC (Certified in Risk and Information Systems Control): The premier certification for risk management.
- CISM (Certified Information Security Manager): Focuses on management and strategy.
- CIPP (Certified Information Privacy Professional): Essential if you want to specialize in Data Privacy laws like GDPR.
3. The “Don’t Bother” List for GRC
- OSCP (Offensive Security Certified Professional): This is for penetration testers. It is incredibly difficult and largely irrelevant to GRC.
- CEH (Certified Ethical Hacker): Generally not respected in the GRC domain; your time is better spent on ISACA certifications.
Phase 4: How to Get GRC Experience Without a Job
You can’t get a job without experience, but you can’t get experience without a job. Here is how to break the loop:
- Volunteer Audits: Non-profits often lack security governance. Offer to help them draft a simple Acceptable Use Policy or perform a basic vendor risk assessment.
- The “Home Lab” for GRC: Create a mock company. Write a mock policy. Perform a mock risk assessment on your own household network. Document these in a portfolio.
- Join ISACA: The Information Systems Audit and Control Association (ISACA) is the #1 networking hub for GRC professionals. Join your local chapter.
Frequently Asked Questions (FAQ)
Is GRC a technical role?
GRC is considered a semi-technical role. While you need to understand technical concepts (like encryption or cloud storage) to assess risk, you generally do not need to configure hardware or write code.
Do I need a degree for GRC?
No. While a degree helps, many GRC professionals transition from other fields using certifications (like Security+) and transferable experience from sectors like law, finance, or operations.
What is the average salary for an entry-level GRC Analyst?
As of 2025, entry-level GRC Analyst salaries typically range from $75,000 to $95,000, depending on location and industry, often higher than entry-level helpdesk roles.
Which GRC framework should I learn first?
Start with NIST CSF (Cybersecurity Framework). It is free, widely used in the US and Canada, and easier to understand for beginners than ISO 27001.
Ready to start your pivot? Transitioning to GRC is about leveraging your “business brain” in a technical world. The industry needs translators, people who can explain risk to the board of directors. That person could be you.
Download our Free GRC Checklist PDF
Relevant Video Resource: … How I Landed a GRC Role in Cybersecurity w/ No Experience …


